Accessing Somebody Else’s Google Calendar: A Complete Information (Moral Issues Included)
Associated Articles: Accessing Somebody Else’s Google Calendar: A Complete Information (Moral Issues Included)
Introduction
On this auspicious event, we’re delighted to delve into the intriguing matter associated to Accessing Somebody Else’s Google Calendar: A Complete Information (Moral Issues Included). Let’s weave attention-grabbing info and supply recent views to the readers.
Desk of Content material
Accessing Somebody Else’s Google Calendar: A Complete Information (Moral Issues Included)
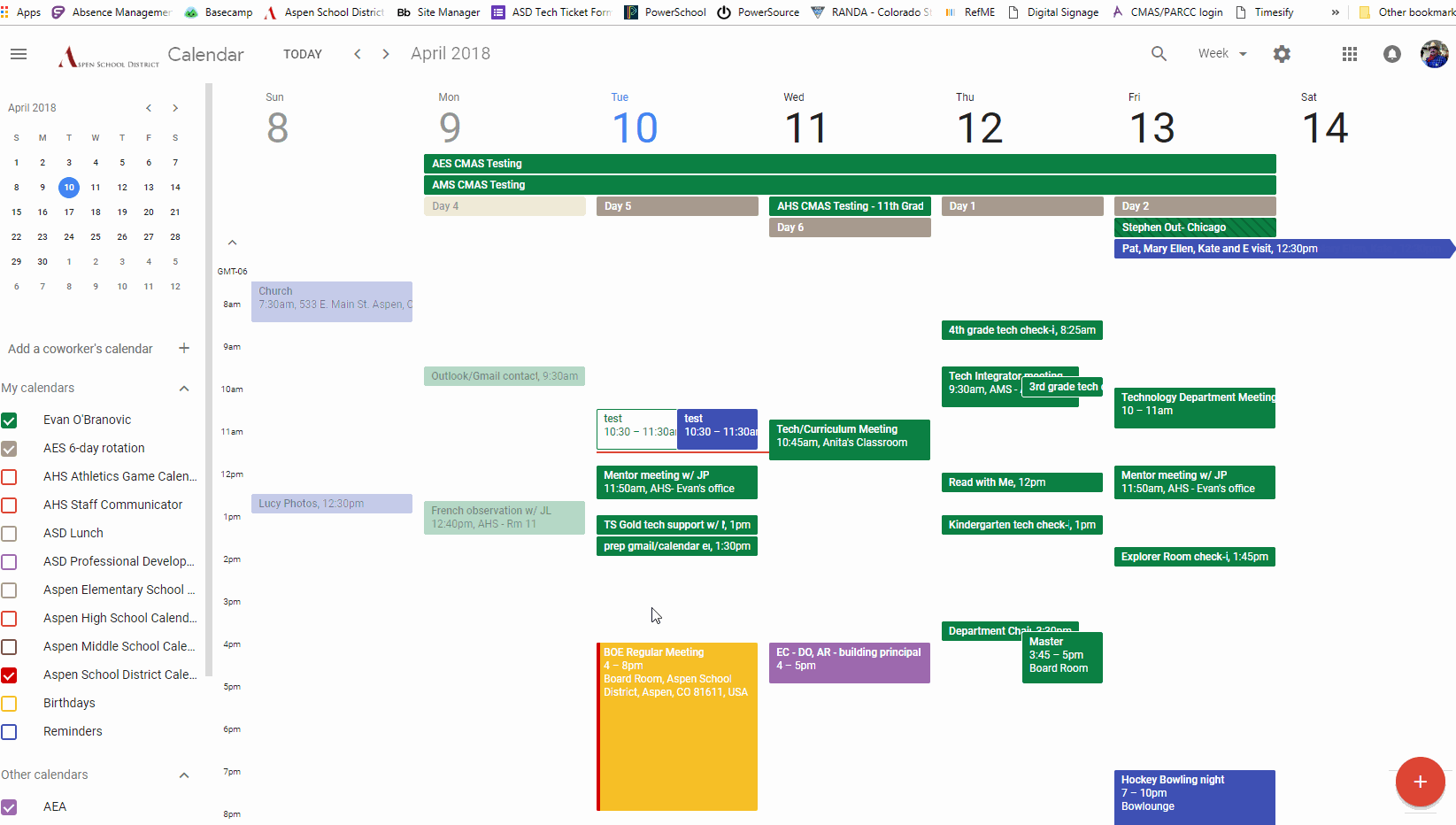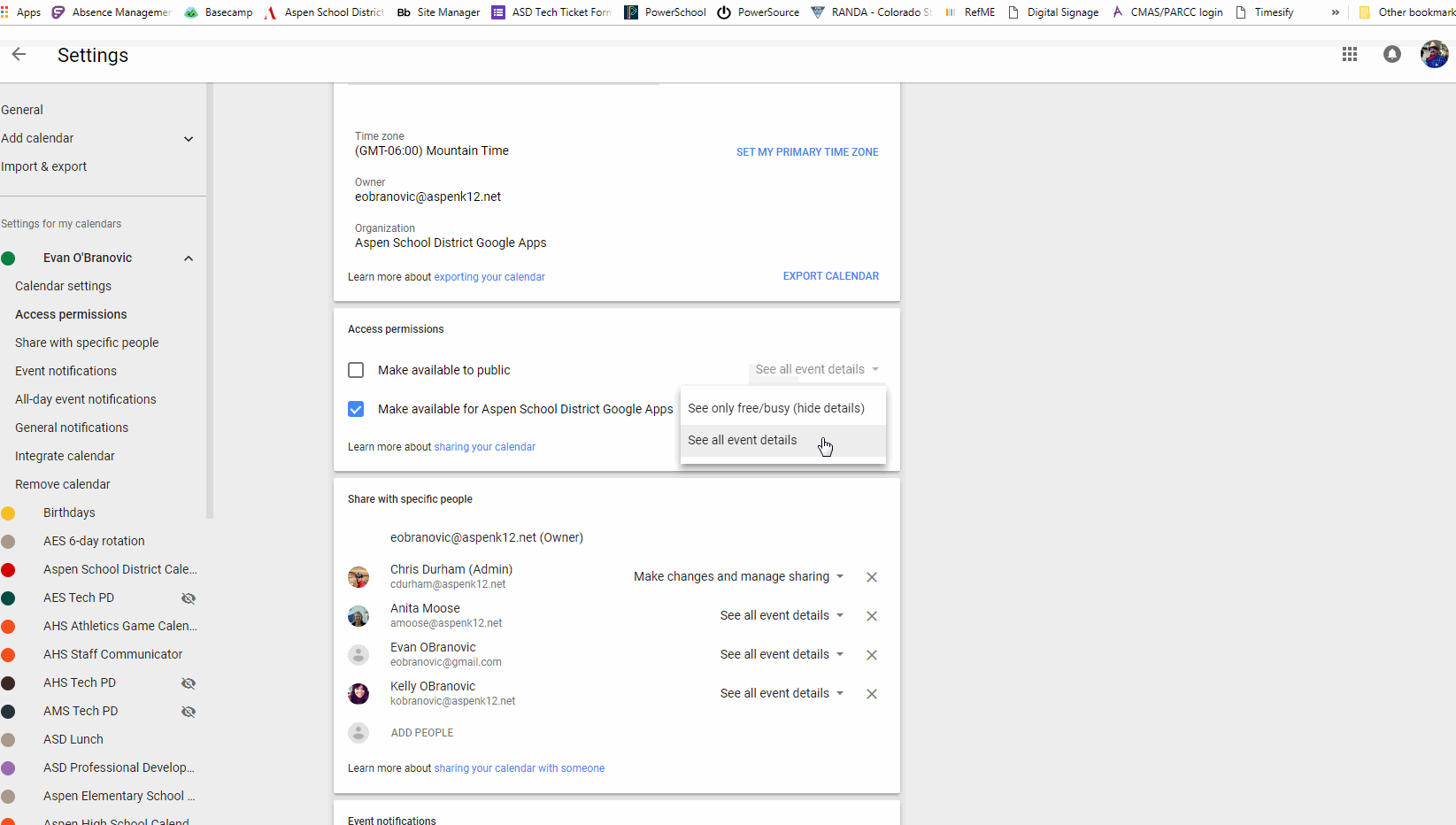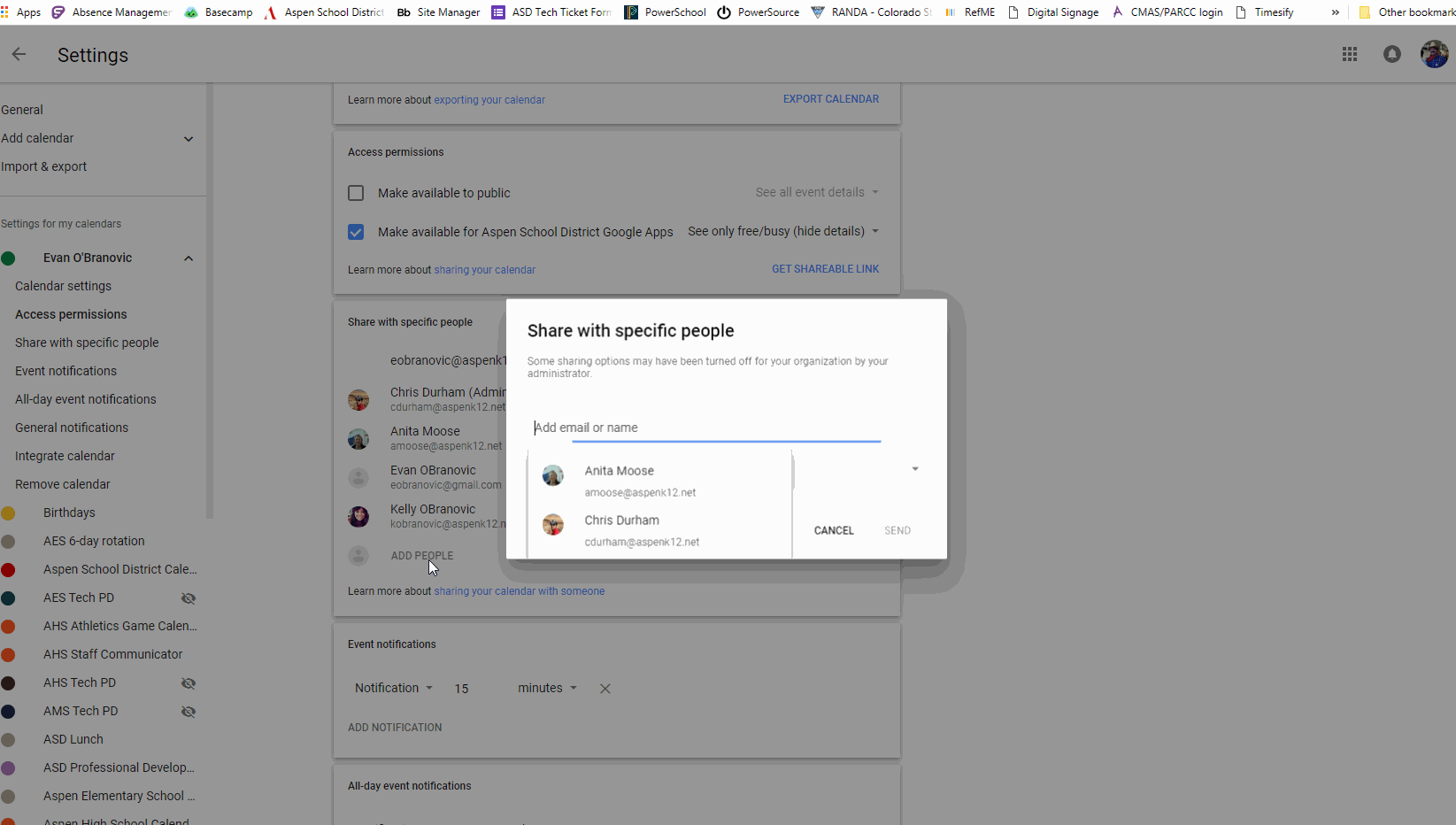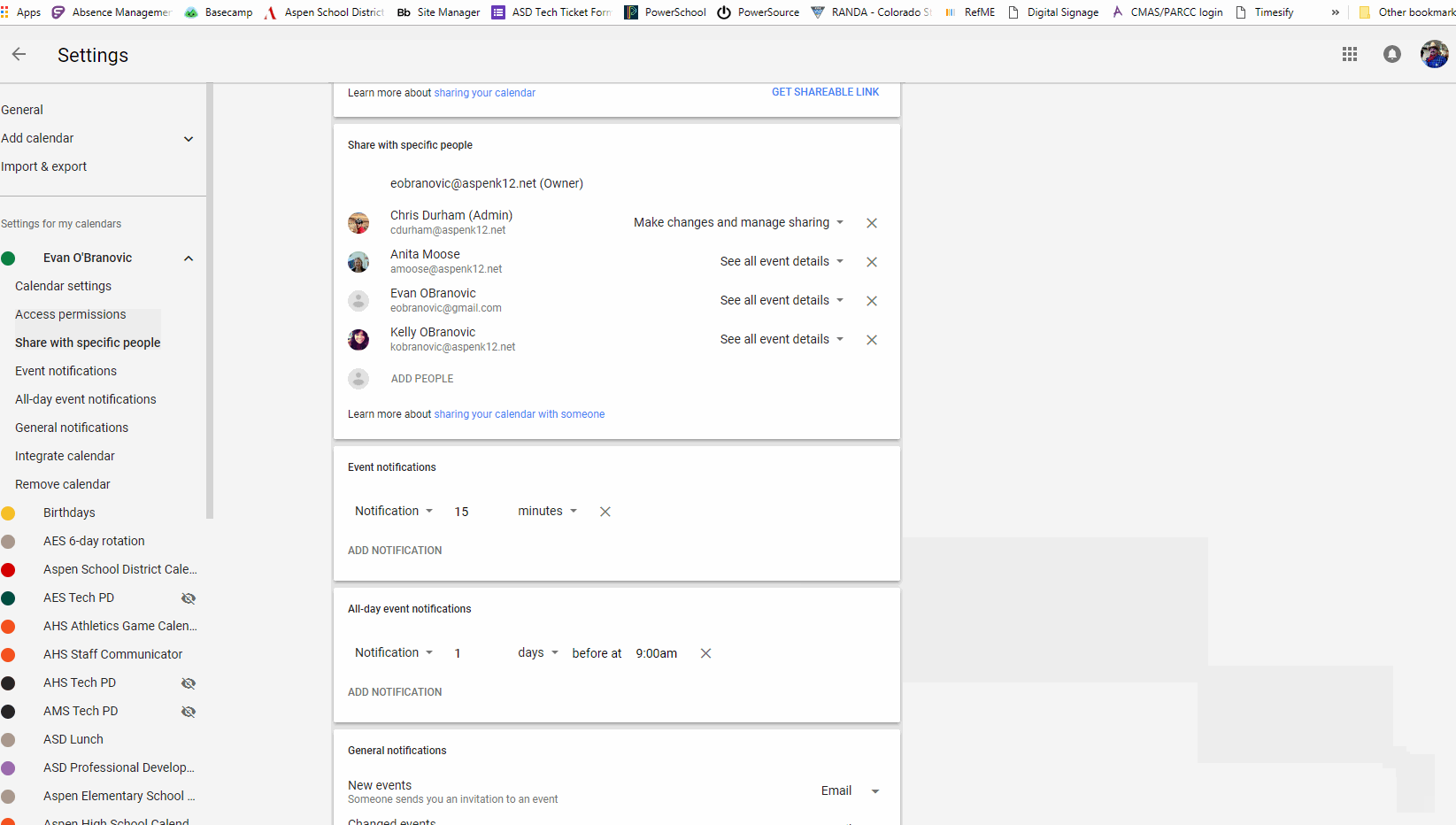
Accessing another person’s Google Calendar with out their specific permission is a critical breach of privateness and doubtlessly unlawful. This text is written for informational functions solely, to clarify the technical limitations and moral implications concerned. We strongly advise towards making an attempt to entry anybody’s Google Calendar with out their consent. Doing so can result in extreme penalties, together with account suspension, authorized motion, and harm to private relationships.
This text will discover the assorted strategies folks would possibly try and entry a Google Calendar and clarify why they’re ineffective or unethical. We will even focus on authentic methods to share calendar info with consent.
Strategies That DON’T Work (and Why):
Many on-line searches result in purported "hacks" or "tips" to entry somebody’s Google Calendar. These are nearly universally false and infrequently harmful. This is why:
-
Third-Occasion Apps and Extensions: Quite a few web sites and app shops declare to supply software program that may entry somebody’s Google Calendar with out their information. These are nearly at all times scams or malware. Google’s safety measures are sturdy, and unauthorized entry is extraordinarily tough. Downloading such software program dangers infecting your system with viruses or spy ware, exposing your individual private info.
-
Phishing and Social Engineering: Makes an attempt to trick somebody into revealing their Google account credentials are unlawful and unethical. Phishing emails or messages pretending to be from Google or different authentic sources could attempt to lure you into coming into your login particulars. By no means reply to suspicious emails or click on on unfamiliar hyperlinks.
-
Password Guessing or Brute-Pressure Assaults: Cracking somebody’s Google account password is very unlikely to succeed attributable to Google’s refined safety measures, together with multi-factor authentication (MFA). Even when profitable, it is a critical crime with important authorized ramifications.
-
Exploiting Vulnerabilities: Looking for and exploiting safety flaws in Google’s methods is illegitimate and unethical. Google actively works to patch vulnerabilities, and making an attempt to take advantage of them is a critical offense.
-
Accessing Shared Gadgets: Whilst you would possibly see a calendar on a shared system, this solely reveals calendars which have been explicitly shared with the consumer profile on that system. It would not grant entry to different accounts.
Why These Strategies Fail:
Google’s safety infrastructure is designed to stop unauthorized entry. Key options defending consumer knowledge embrace:
- Two-Issue Authentication (2FA): This requires a second verification step past the password, reminiscent of a code despatched to a cellphone or electronic mail.
- Account Restoration Measures: Google employs sturdy mechanisms to stop unauthorized entry, requiring verification by means of numerous strategies earlier than granting entry to a compromised account.
- Common Safety Updates: Google always updates its methods to deal with potential vulnerabilities and shield consumer knowledge.
- Knowledge Encryption: Google encrypts consumer knowledge, making it extraordinarily tough to entry with out the proper credentials.
Authentic Methods to Entry Calendar Data (with Consent):
The one moral and authorized technique to see somebody’s Google Calendar is with their specific permission. This is how:
-
Sharing a Calendar: The proprietor of the Google Calendar can share it with particular people or teams. They’ll select totally different permission ranges, reminiscent of "view solely" or "edit." That is the usual and really helpful methodology for sharing calendar info.
-
Public Calendars: Some people could select to make their calendars publicly accessible. Nevertheless, that is uncommon for private calendars, and even public calendars usually have restricted viewing permissions.
-
Delegated Entry: A calendar proprietor can grant one other consumer "delegate" entry, which permits the delegate to handle appointments and occasions on their behalf. That is usually utilized in skilled settings, reminiscent of an assistant managing a supervisor’s calendar.
-
Third-Occasion Apps with Express Permissions: Some authentic calendar functions permit customers to attach and share calendars with specific consent. All the time guarantee these apps are respected and have clear privateness insurance policies earlier than granting entry. Examine opinions and guarantee they’ve acceptable safety measures in place.
Moral Issues:
Respecting somebody’s privateness is paramount. Unauthorized entry to their Google Calendar, whatever the methodology, is a critical breach of belief and a violation of their privateness rights. Contemplate the potential penalties:
- Injury to Relationships: Discovering somebody has snooped in your calendar can severely harm belief and relationships.
- Authorized Ramifications: Unauthorized entry to somebody’s account can result in civil or prison expenses.
- Reputational Hurt: Being caught accessing somebody’s calendar with out permission can have important repercussions in your private {and professional} fame.
Conclusion:
Accessing somebody’s Google Calendar with out their consent is unethical, doubtlessly unlawful, and intensely tough attributable to Google’s sturdy safety measures. All the time prioritize moral concerns and respect particular person privateness. If it’s worthwhile to entry somebody’s calendar info, ask for his or her permission and make the most of the authentic sharing strategies described above. Bear in mind, the implications of unauthorized entry far outweigh any perceived profit. This text serves as a reminder of the significance of on-line privateness and the intense repercussions of violating it. All the time act responsibly and ethically when coping with on-line accounts and private info.






Closure
Thus, we hope this text has offered worthwhile insights into Accessing Somebody Else’s Google Calendar: A Complete Information (Moral Issues Included). We respect your consideration to our article. See you in our subsequent article!